Explain the Different Type of Phishing Technique
Now lets move to other types. The types of phishing attacks are deceptive phishing spear phishing clone phishing website phishing and CEO fraud which are described as below.
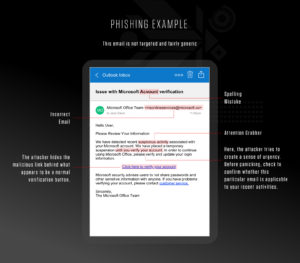
What Is Spear Phishing Definition With Examples Crowdstrike
Phishing Emails Dont Get Reeled In.

. Our SOAR platform allows you to orchestrate automate responses to phishing threats. Easily Train Large Small Workforces Remotely. Today phishing can use multiple communication methods and has evolved from low-level schemes to the sophisticated targeting of individuals and organizations.
This is the typical phishing email that is designed to mimic a legitimate company. Other than email and website phishing theres also vishing voice phishing smishing SMS Phishing and several other phishing techniques cybercriminals are constantly coming up with. 13 Types of Phishing Attacks.
Ad 91 Of Data Breaches Start With Spear Phishing Attacks On Organizations. 2Whaling Whaling is an even more. IDGs latest report with Carbonite Webroot dives into the latest phishing data.
Explain Different Types of Phishing Techniques By Ra_Tianna162 21 Apr 2022 Post a Comment Minimal or no dollar amounts assigned to land non-depreciable land. Attackers use the information to steal money. 1 Such as whether the criminal disperses his message via email or instant messaging platform whether he tries to obtain the information via malware like a key-logger.
Take Your Online Phishing Recognition Training from Boring to Brilliant. Ad If you think phishing is only. The first spear phishing describes malicious emails sent to a specific person.
Phishing comes in many forms from spear phishing whaling and business-email compromise to clone phishing vishing and snowshoeing. There are other techniques used by phishers to lure victims such as. There are two other more sophisticated types of phishing involving email.
Ad Download the full report to read the IDG insights for protecting against phishing. Phishing is a type of social engineering attack often used to steal user data including login credentials and credit card numbers. Ad Interactive Training with Gamified Endings.
Deceptive phishing is the most common type of phishing. Here are eight different types of phishing attempts you might encounter. Up to 20 cash back Types of phishing attacks range from classic email phishing schemes to more inventive approaches such as spear phishing and smishing.
In this technique for phishing by email is used. Get a Free Trial. Heres how to recognize each type of.
SaaS Phishing phishers can steal login credentials to a Software as a Service SaaS site to gain. In this case an attacker attempts to obtain confidential information from the victims. IDGs latest report with Carbonite Webroot dives into the latest phishing data.
So this was a very simple example for spear phishing. Symantec reveals in its Internet Security Threat Report that around 65 of cybercriminals primarily prefer spear phishing for targeted attacks. All have the same purpose.
Ad Download the full report to read the IDG insights for protecting against phishing. Phishing via phone call and text message respectively. It occurs when an attacker masquerading.
Find Out What Percentage Of Your Employees Are Vulnerable. Other types of phishing include clone phishing snowshoeing social media phishing and.
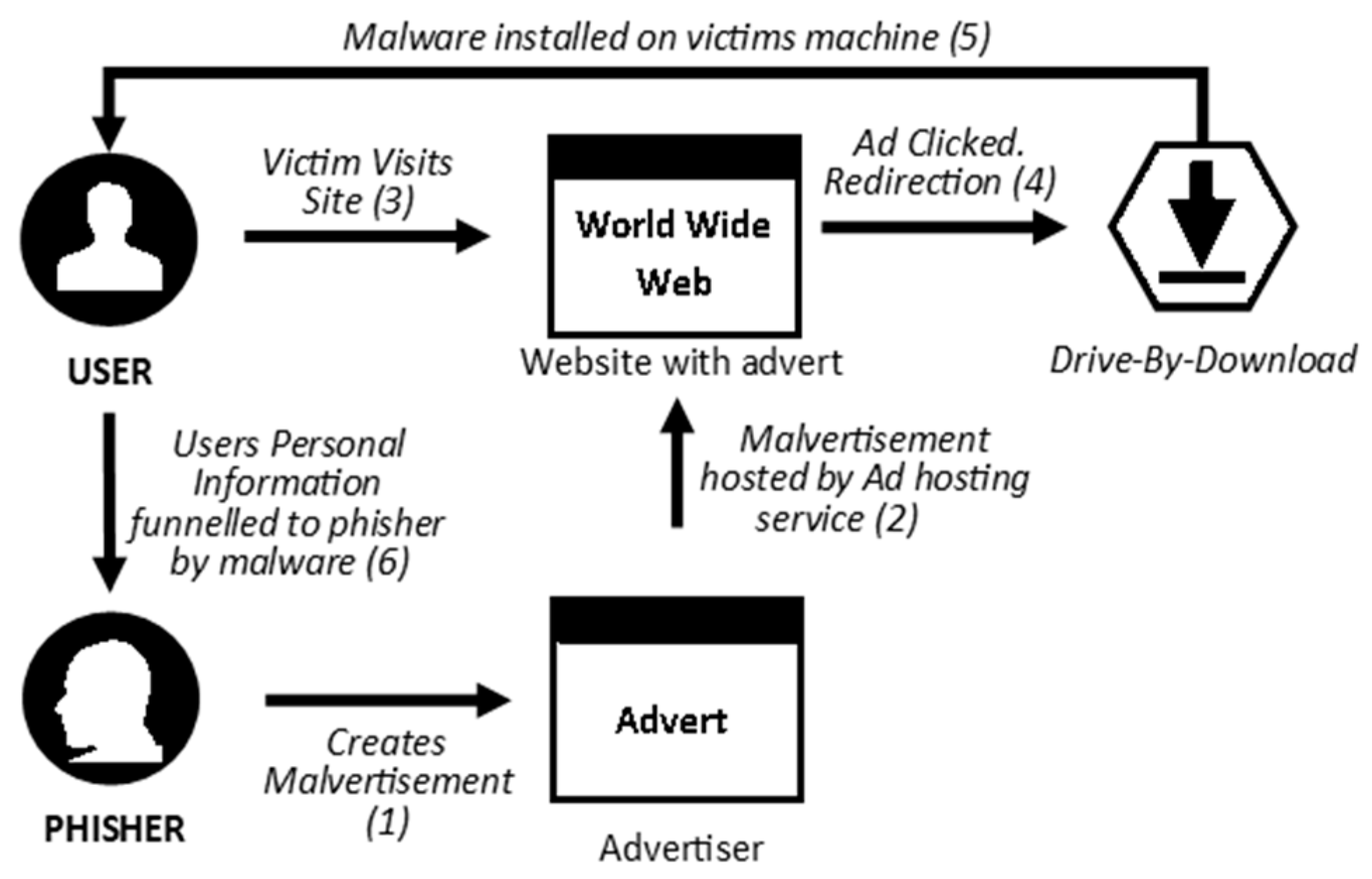
Future Internet Free Full Text Phishing Attacks Survey Types Vectors And Technical Approaches Html
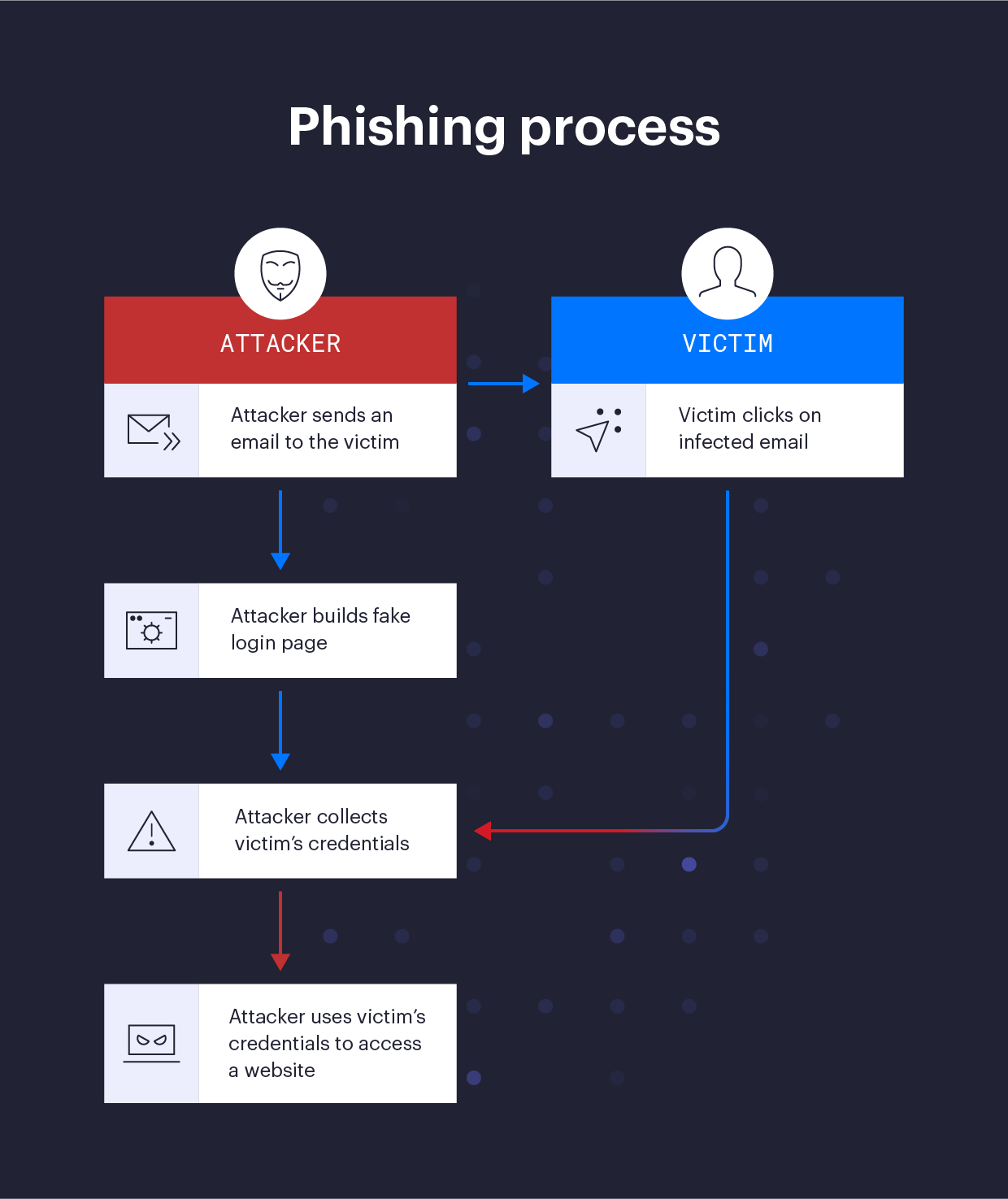
Phishing Attacks Types Prevention And Examples
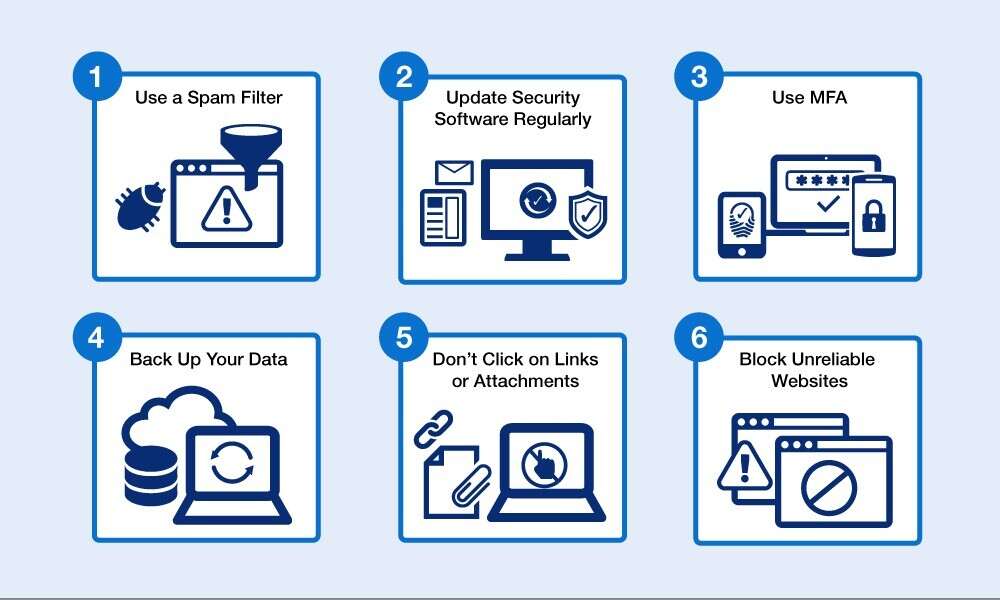
What Is Phishing Avoiding Email Scams Attacks Fortinet
Email Phishing Vishing Other Types Of Attacks Webroot
Why We Fall For Phishing Emails And How We Can Protect Ourselves

Types Of Phishing Attacks Social Media Infographic Spear Phishing Cyber Security
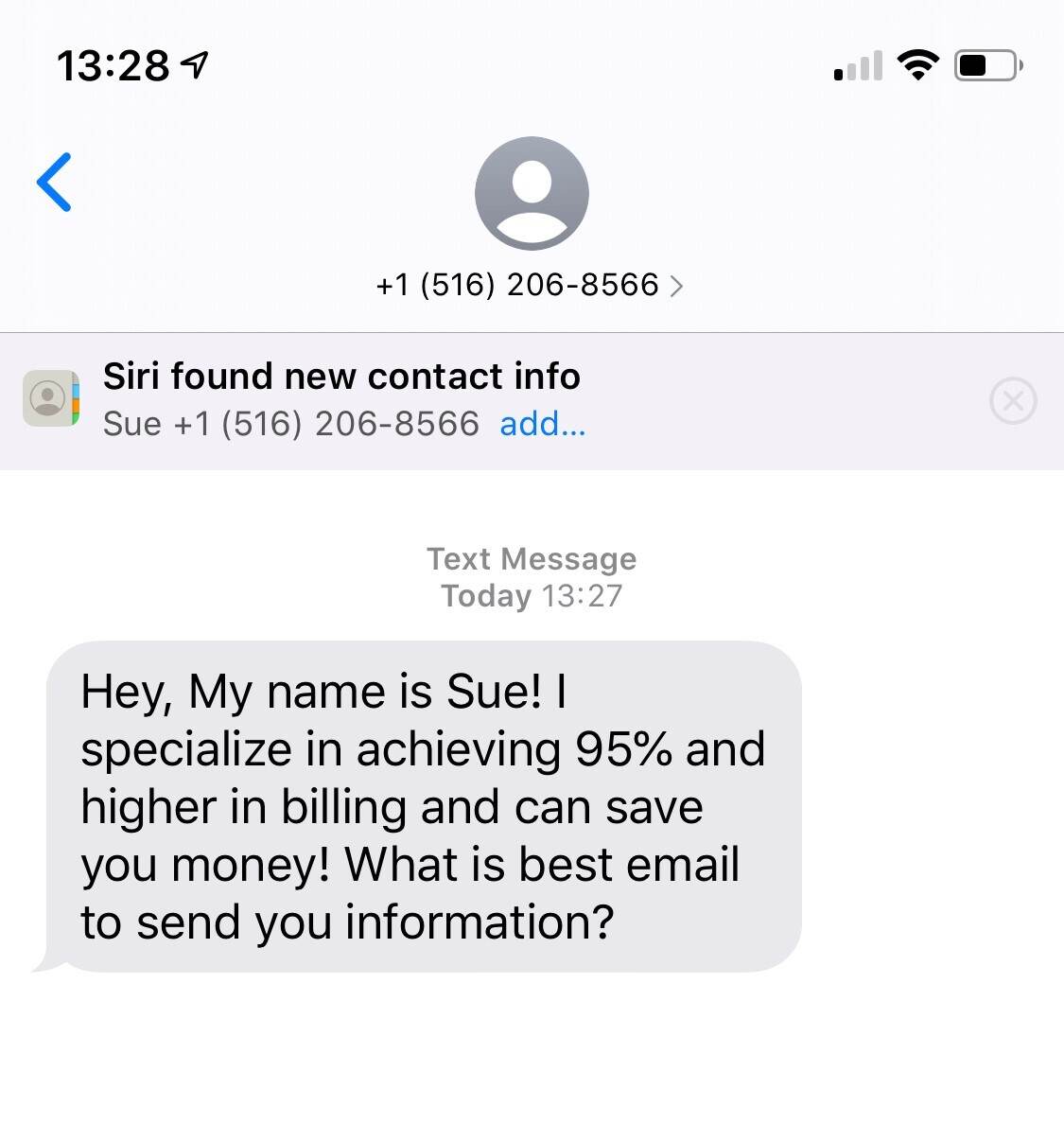
What Are The Different Types Of Phishing

What Is Phishing Examples Prevention Terranova Security

What Are The Different Types Of Phishing
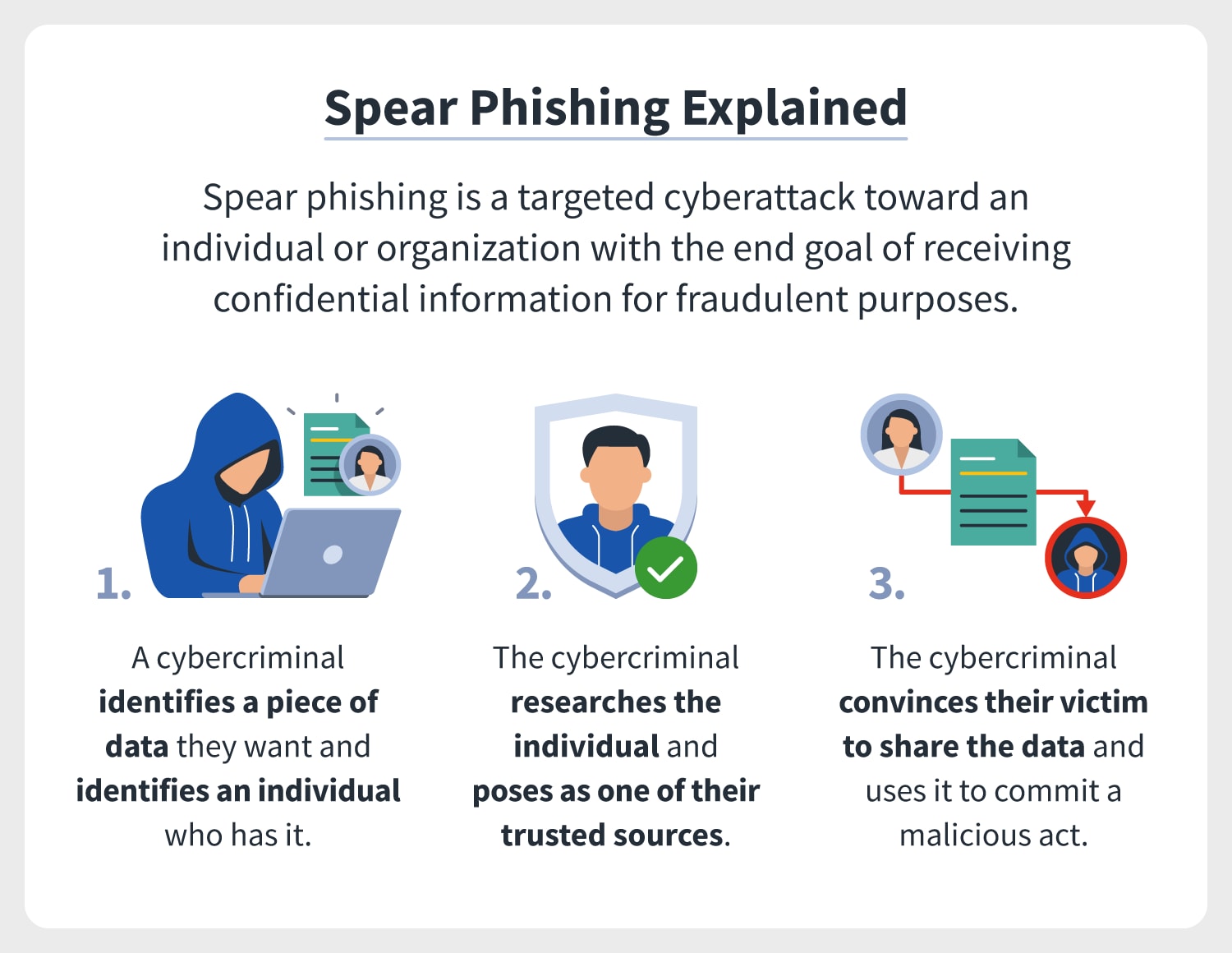
Spear Phishing A Definition Plus Differences Between Phishing And Spear Phishing Norton

Spear Phishing Vs Phishing Key Differences And Similarities Toolbox It Security
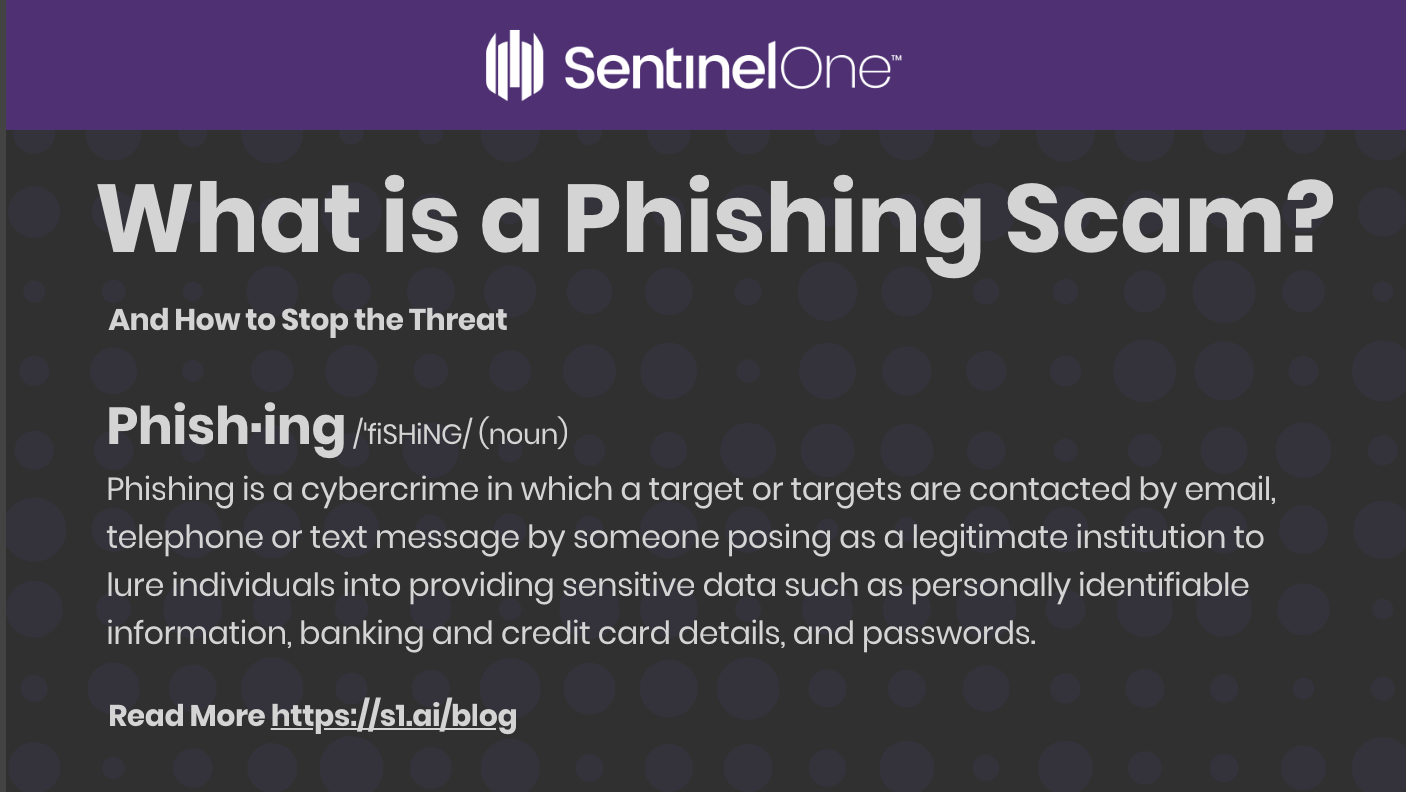
Phishing Scams How To Recognize Avoid Them Sentinelone

Phishing Awareness Best Practices For Email Testing Currentware

6 Common Phishing Attacks And How To Protect Against Them

What Is Phishing Avoiding Email Scams Attacks Fortinet

Types Of Phishing What It Is An How To Prevent It

Spear Phishing A Definition Plus Differences Between Phishing And Spear Phishing Norton

6 Common Phishing Attacks And How To Protect Against Them
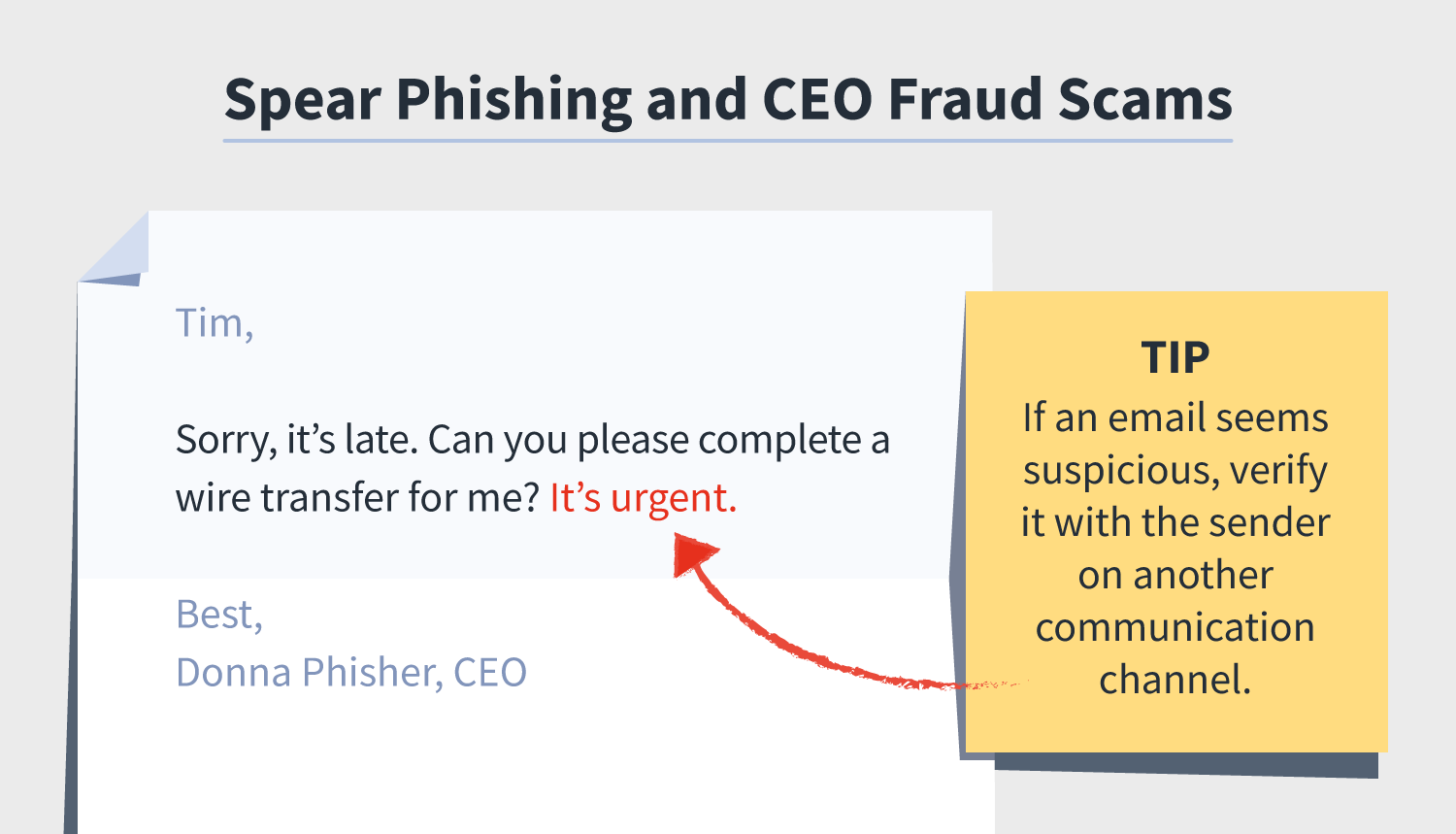
Spear Phishing A Definition Plus Differences Between Phishing And Spear Phishing Norton
Comments
Post a Comment